Jamming and spoofing detection performance at Jammertest 2025 in Andøya, Norway
Jammertest 2025 highlighted one truth: resilient GNSS isn’t built in the lab, it’s proven in the field. And u-blox delivered.
Introduction
Jammertest 2025 is an international live-field event dedicated to evaluating the resilience of GNSS systems against interference, jamming, and spoofing. Held on the remote island of Andøya in Norway, it brings together regulators, researchers, and technology leaders to test positioning technologies under RF conditions that go far beyond controlled laboratory setups. u-blox is participating to demonstrate its leadership in secure and resilient positioning, a critical capability as GNSS is increasingly embedded in automotive and industrial applications. Our goal at Jammertest 2025 is not only to validate the performance of our solutions in demanding environments but also to challenge our own capabilities and gather insights that drive incremental improvements for future products.
Insights from Jammertest 2025
The testing program at Jammertest 2025 subjected GNSS receivers to a wide variety of interference and spoofing challenges. High-power campaigns included continuous wave, sweeping, and PRN jamming across multiple bands such as L1, L2, L5, and L6, with power levels reaching up to 50 watts. These scenarios replicated extreme denial conditions where one or more frequency bands were heavily disrupted. Alongside this, more localized interference was introduced through handheld jammers, while mobile spoofing created false trajectories and position shifts during dynamic driving tests. Time manipulation attacks added further stress by forcing sudden clock jumps ranging from minutes to years, highlighting the risks for applications dependent on precise synchronization.
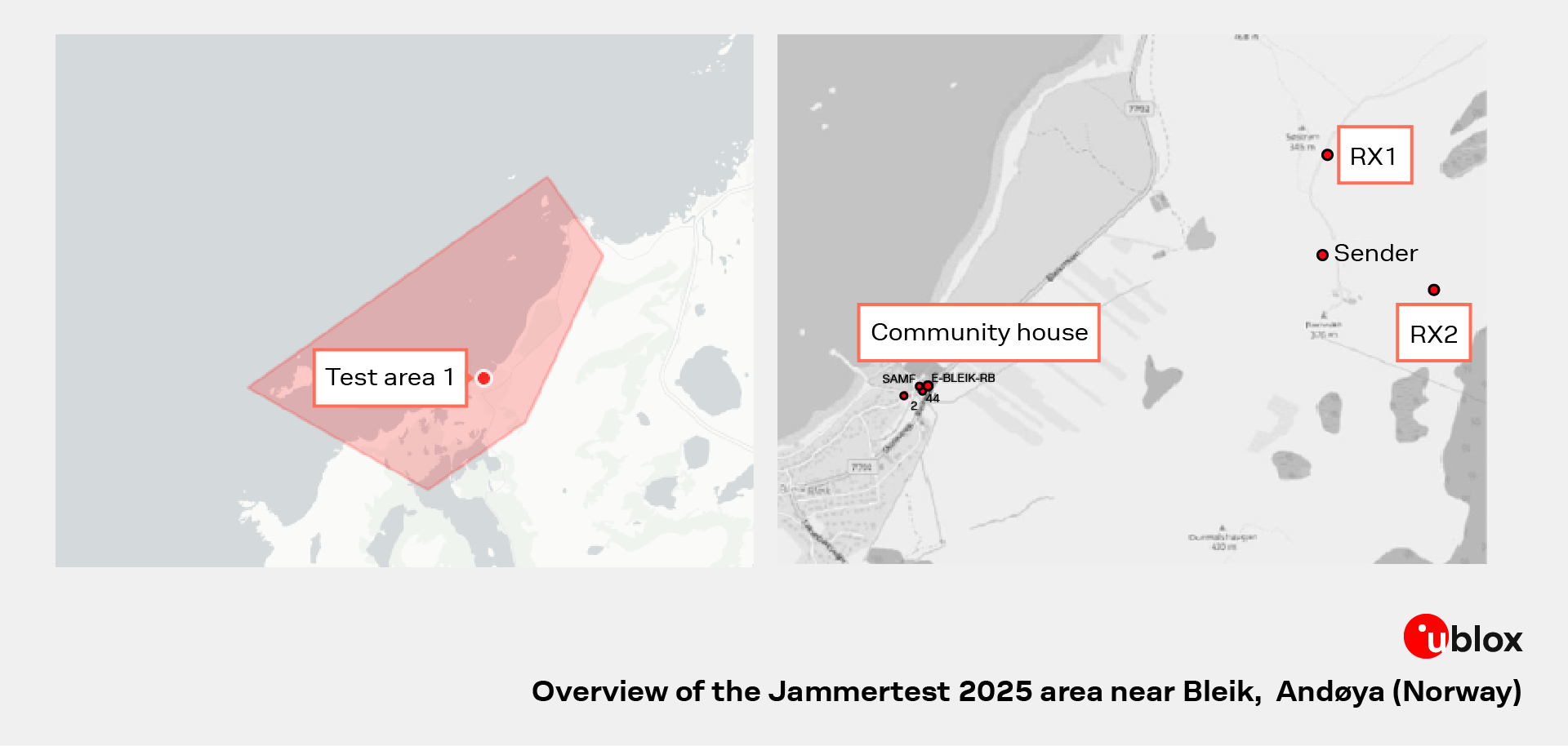
Test Area 1 (left) hosted both static and dynamic drive routes. The Community House, RX1, and RX2 sites (right) served as key transmission points for jamming, spoofing, and meaconing, creating realistic multi-source interference conditions.
u-blox technology demonstrated how such threats can be mitigated in practice. Spoofing detection relies on a hybrid strategy that monitors consistency across constellations, flags sudden jumps, and integrates authentication services such as Galileo OSNMA to confirm signal integrity. For jamming, advanced RF filtering and suppression algorithms work together with intelligent multi-band management so that when one frequency is denied, positioning continues on others. This approach ensures continuity and trusted navigation performance in the harshest RF environments.
Join u-blox experts for an exclusive webinar on insights
from Jammertest 2025 in Andøya, Norway.
Key Results from Jammertest 2025
Each test at Jammertest 2025 was designed to evaluate how the u-blox ZED-X20P receiver performs under specific jamming and spoofing challenges. All tests were performed using the u-blox ANN-MB2 multi-band antenna, ensuring consistent signal quality and representative performance under live-field conditions. The following summaries highlight the most significant findings from the campaign.
1. Jamming Gauntlet (Test 1.18.5, 1.18.7, 1.18.13, 1.18.15)
| 1.18.5 | CW signal drift: 1545 to 1620 MHz, 15 minutes sweep time |
| 1.18.7 | CW signal drift: 1620 to 1545 MHz, 15 minutes sweep time |
| 1.18.13 | 50 W drift: 1150 to 1300 MHz, with CW and sweep time of 15 minutes |
| 1.18.15 | 50 W drift: 1300 to 1150 MHz, with CW and sweep time of 15 minutes |
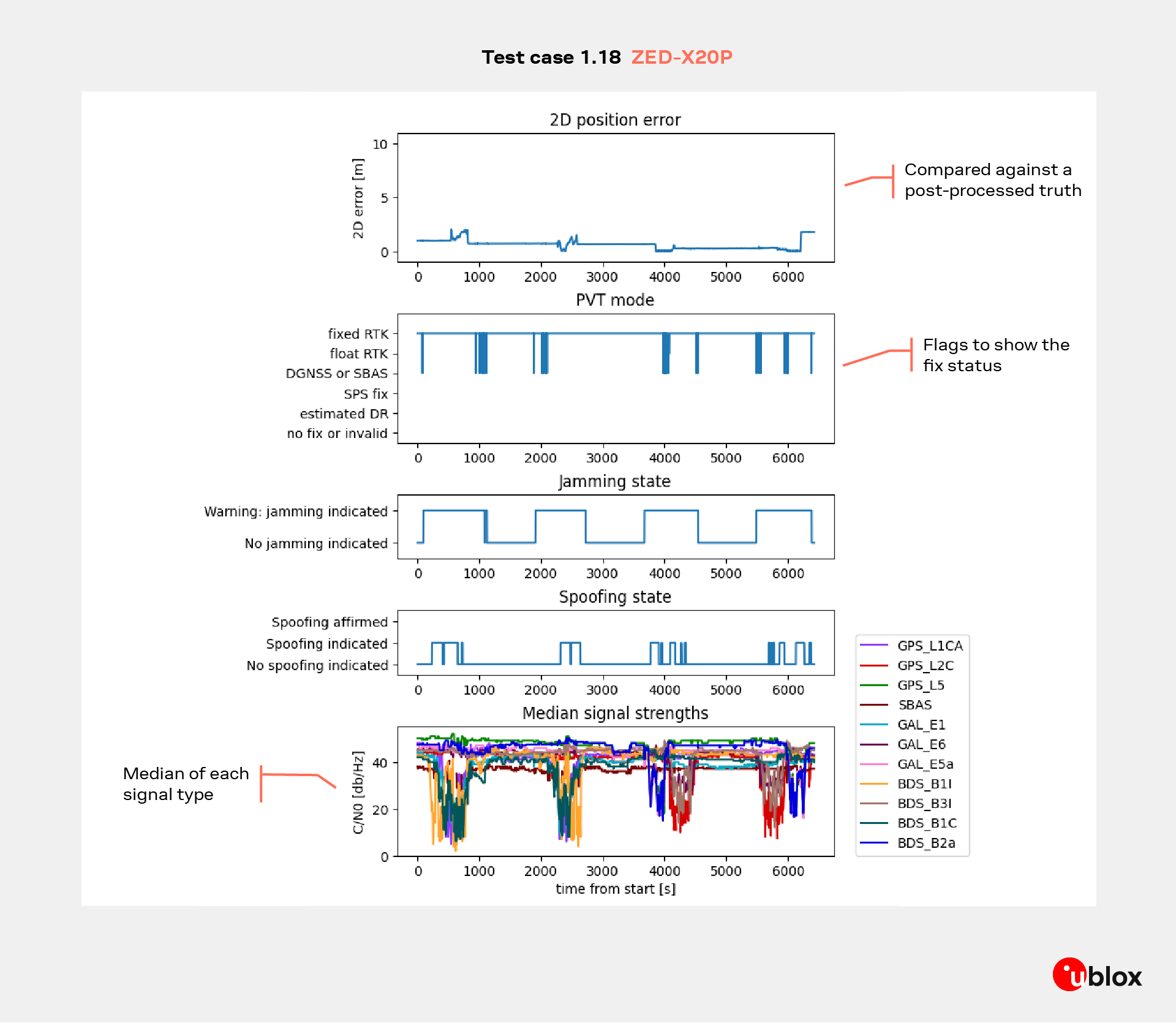
These tests ran a sequential, high-power jamming campaign across individual frequency ranges to simulate targeted denial of service. Continuous-wave and drifting CW sweeps (47 dBm / ≈50 W) covered segments from roughly 1150 MHz to 1620 MHz, selectively impairing GPS L1 (≈1575 MHz), L2 (≈1227 MHz), L5 (≈1176 MHz) and Galileo E6 (≈1278 MHz) at different times. The setup included both static and dynamic driving phases, allowing the team to observe receiver behavior while stationary and while in motion under live-sky conditions. The goal was to evaluate whether a receiver could sustain navigation when one band at a time was effectively taken offline.
Despite the intense interference, the u-blox ZED-X20P maintained continuous navigation, seamlessly switching to unaffected frequencies. The actual positioning accuracy remained at the centimeter level, consistent with RTK performance, although the plot shows short variations of up to 2 meters during vehicle motion. These apparent deviations are due to truth-reference degradation rather than receiver instability under strong RF load and dynamic conditions, the reference system’s precision temporarily decreases, making the X20P appear less accurate than it truly is.
During some of these runs, both jamming and spoofing detection flags were triggered, even though only jamming was applied. This behavior reflects u-blox’s safety-first approach to signal integrity, where the receiver is intentionally conservative in raising alerts so that customers are aware of any potential signal anomalies. In real-world conditions, interference patterns can sometimes mimic spoofing-like behavior, and the system is designed to encourage caution. Importantly, these alerts do not compromise navigation performance, even while flagging potential threats, the ZED-X20P continued to deliver reliable and accurate position outputs, demonstrating that robust detection and dependable positioning can coexist. Nevertheless, users should treat a valid fix under flagged conditions with awareness. It indicates strong mitigation capability, but also that the environment is degraded and caution is advised.
Result summary: Stable RTK or DGNSS1 positioning across all partial-band jamming scenarios; no total loss of navigation observed, with minor dynamic-phase variations explained by reference-system limitations rather than receiver performance.
Correction data is received but RTK ambiguity resolution is temporarily unavailable
2. Replay Attack “Meaconing Mayhem” (Test 3.4.2 )
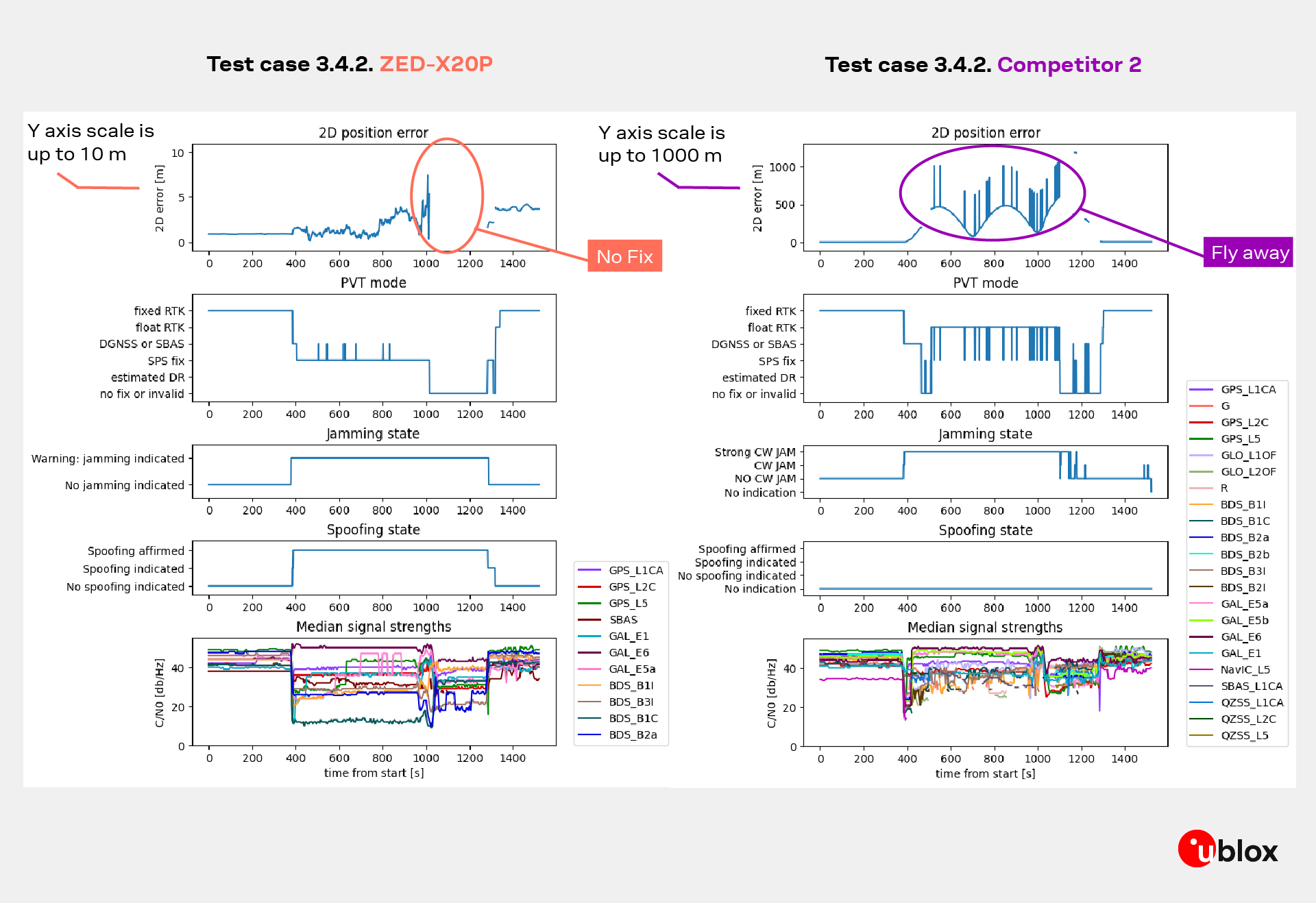
In this scenario, a stationary meaconing transmitter (RX1) continuously retransmitted live GNSS signals, while a mobile spoofing source (“Winnie the Spoof”) introduced additional deceptive signals from a different location. The combination of a stable meaconing signal and a dynamic spoofing source created a highly complex interference environment with multiple false signal origins.
The test aimed to observe how the receiver behaves when exposed simultaneously to time-delayed legitimate signals (meaconing) and artificially generated spoofing signals with varying power and motion patterns. The test included both static and dynamic driving phases, enabling evaluation of receiver behavior while stationary and in motion as the spoofed power level rose.
At the start of the test, the u-blox ZED-X20P tracked authentic signals normally, maintaining RTK accuracy. As the false-signal power increased, the receiver recognized the inconsistency between constellations and entered a no-fix2 state rather than reporting a deceptive position. Multiple independent spoofing-detection layers confirmed the event, resulting in a spoofing affirmed state.
A slight offset in the X20P’s position-error plot is visible near the end of the scenario; this is linked to truth-reference degradation, the external ground-truth system loses precision as the vehicle moves under severe RF load, making its accuracy unreliable toward the end of the run. The X20P’s navigation solution itself remained internally stable and trustworthy throughout
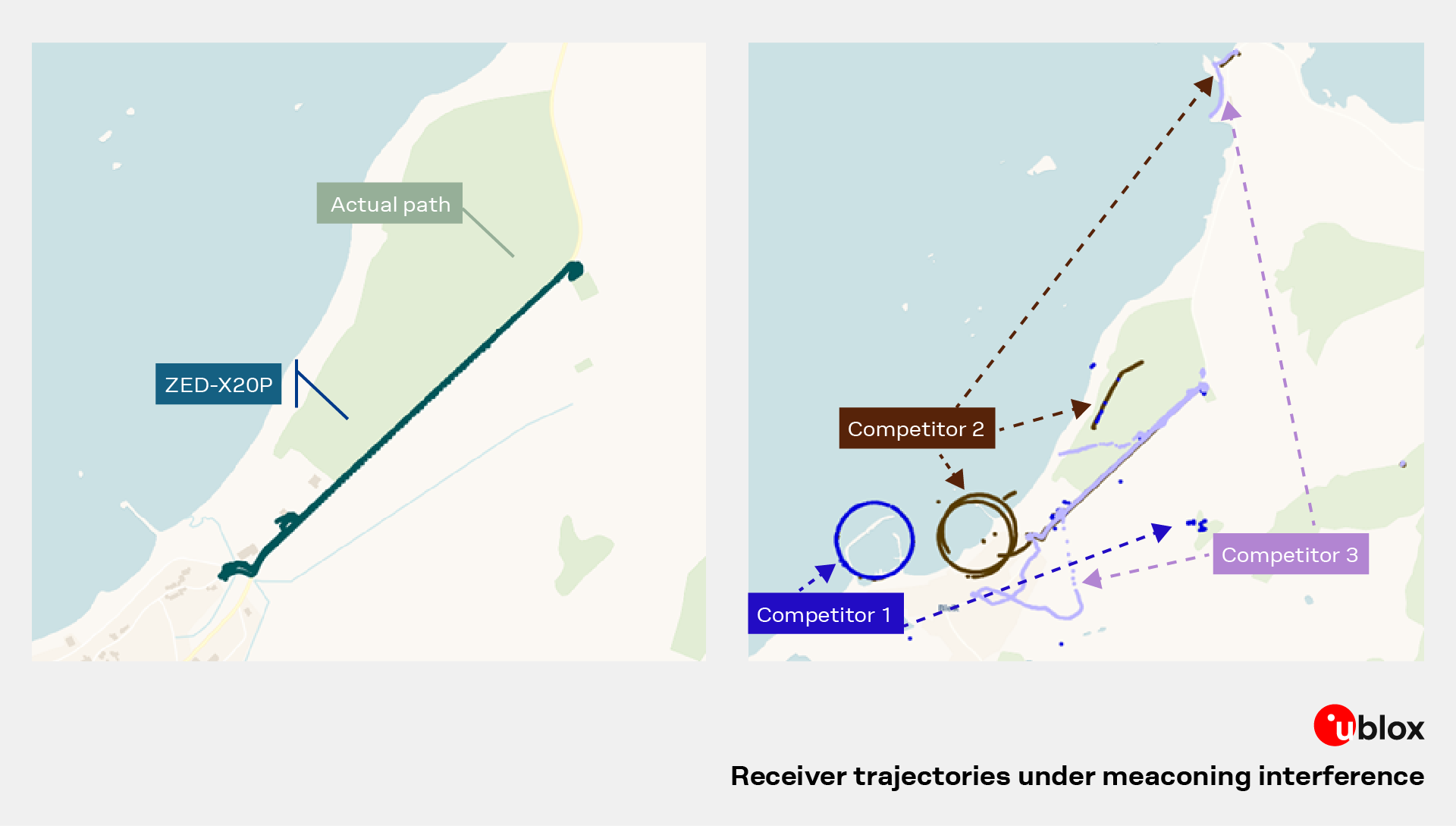
By contrast, other receivers under test immediately followed the meaconed signals once the jamming phase ended, as seen in the comparison tracks that “fly away” from the real path. In the same conditions, the ZED-X20P trace remained steady and terminated gracefully once signal trust could no longer be guaranteed, a deliberate, integrity-driven design choice.
Result summary: ZED-X20P initially used authentic signals, detected the meaconing power ramp, entered no-fix instead of false-position mode, and correctly affirmed spoofing through multiple detection mechanisms; observed end-of-test offset originates from reference degradation, not receiver drift.
2Position withheld because signal integrity can’t be guaranteed
3. Coherent Spoofing “The Phantom Route” (Tests 2.3.5 & 2.3.8)
In this pair of simulated-driving tests a stationary spoofer broadcasts authentic-looking GNSS signals using true (broadcast) ephemerides to create a coherent, position-altering attack. Test 2.3.5 replayed a GPS-only route (L1 C/A, L2C, L5) while 2.3.8 replayed the same route using Galileo (E1, E5, E6). There was no jamming in these scenarios: initial time and position were true (sub-100 ns timing error at the start), and the spoofed signals were designed to be highly convincing, the classic test of whether a receiver will be led to follow a false trajectory.
The field results reveal a clear contrast in receiver’s behavior under coherent spoofing conditions. The ZED-X20P plots show a stable trajectory that follows the true route until the spoofed signals strengthen at which point the receiver correctly recognizes the deception, raises spoofing alerts, and transitions to a no-fix state rather than reporting a false position. Its detection layers affirm spoofing and protect integrity without compromising reliability.
In comparison, the competitor receivers display trajectories that deviate dramatically from the real path. Once the spoofed signals dominate, their position solutions diverge or loop away from the intended route, demonstrating loss of signal trust. The signal-strength and state plots confirm that these devices continued to navigate using corrupted data, while the ZED-X20P maintained control and situational awareness even in a fully deceptive environment.
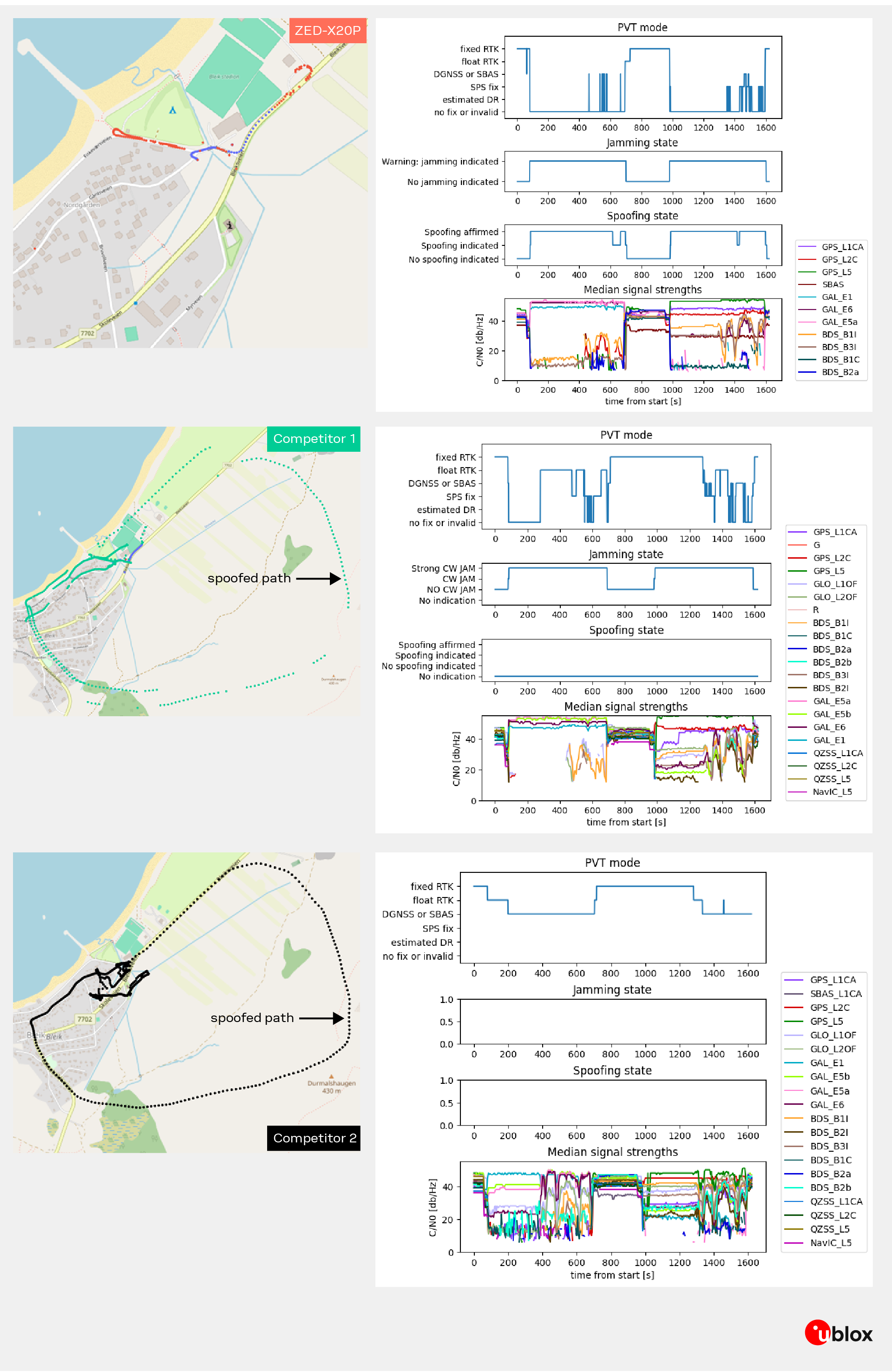
Why this matters: the spoofed signals in these tests are coherent and use authentic satellite orbit and timing data, making them difficult to distinguish from genuine satellites by simple power or C/N₀ checks. The ZED-X20P’s layered detection approach (cross-constellation consistency checks, timing/position sanity filters, correlation-shape monitoring and authentication where available) deliberately favors integrity over continuity: when confidence in the positioning solution falls, the receiver withholds position (no-fix) rather than present a plausible but false location. This conservative response prevents downstream systems from acting on corrupted navigation data and gives operators clear, actionable alarms.
Result summary: Under coherent position spoofing (GPS-only and Galileo-only simulated driving), ZED-X20P detected spoofing and entered a no-fix state, preserving integrity; competing receivers followed the spoofed trajectories and reported false positions.
Key takeaway: In high-fidelity spoofing attacks that closely mimic real GNSS signals, a conservative, multi-layer detection strategy prevents false fixes, sacrificing continuity when necessary to protect safety and trust in the navigation solution.
Conclusion: Proven Resilience, Trusted Positioning
Jammertest 2025 once again demonstrated that the true measure of GNSS resilience is proven in the field, not in controlled laboratory conditions. Across multiple demanding scenarios, from selective multi-band jamming to coordinated meaconing and coherent spoofing, the u-blox ZED-X20P consistently followed the same design philosophy: maintain continuity when it’s safe and protect integrity when it’s not.
When interference struck, the receiver intelligently leveraged unaffected frequencies to keep positioning stable. When spoofing threats appeared, it chose caution entering a no-fix state rather than reporting a deceptive location. Each detection flag, each conservative decision, and each rapid recovery highlighted a system engineered for real-world uncertainty.
The progress showcased this year builds directly on the insights gained from Jammertest 2024, which guided several incremental improvements to spoofing and jamming resilience. The results presented here were achieved using a development version of the ZED-X20P firmware, scheduled for public release in early 2026. The experience from this year’s event will drive the next round of refinements, further strengthening detection logic, authentication handling, and multi-band recovery strategies.
We’ll be sharing deeper insights and detailed analysis in the coming months.
To learn more about our work on secure and interference-resilient GNSS, or to collaborate on future testing initiatives, connect with us for post-event updates and technical deep dives.

Shadman Siddiqu
Senior Technical Marketing GNSS Automotive
Business Unit Positioning, u-blox
Get in touch for orders or any queries: sales@rfdesign.co.za / +27 21 555 8400
Courtesy of u-blox

